
Secure URL algorithms ensure that URLs used for sensitive information, authentication, or secure access are both encrypted and verified. These algorithms protect against unauthorized data access by encoding information in URLs and providing a means to verify its authenticity.
HMAC-SHA (Hash-Based Message Authentication Code with SHA)

Description:
HMAC-SHA is a cryptographic mechanism that combines a secure hash function (such as SHA-1, SHA-256, or SHA-512) with a secret key to generate a unique message digest, often referred to as a signature. This signature ensures the authenticity and integrity of data transmitted via URLs. When used in URLs, the HMAC acts as a digital seal, guaranteeing that the URL has not been altered or tampered with during transmission.
HMAC-SHA does not encrypt the URL content but validates its authenticity, making it especially valuable for APIs, temporary access links, and other secure communication scenarios.
How It Works
Generate the HMAC:
Transmit the URL:
Pros:
High Security:
Fast and Efficient:
Widely Supported:
Tamper Prevention:
Deterministic:
Cons:
Use Case:
Commonly used in APIs and signed URLs for file-sharing services like AWS S3 or Google Cloud.
2. AES (Advanced Encryption Standard)
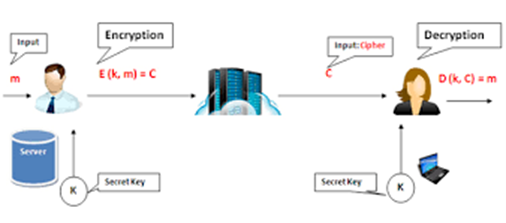
Description
AES (Advanced Encryption Standard) is a widely used symmetric encryption algorithm designed to securely encrypt and decrypt data. It ensures the confidentiality of sensitive information embedded in URLs, making it highly effective in safeguarding access tokens, user IDs, session identifiers, and other critical data transmitted over the web. Since it uses the same secret key for encryption and decryption, AES requires secure key exchange and management to prevent unauthorized access.
AES is recognized for its high performance, adaptability, and robustness. It supports key sizes of 128, 192, and 256 bits, allowing for flexible implementation based on the required security level.
How It Works
Encryption Process:
Decryption Process:
Transmission Security:
Along with HTTPS for secure communication, AES encryption adds an additional layer of protection to ensure that sensitive URL data remains confidential, even if intercepted.
Pros:
Cons:
Use Case:
Encrypting sensitive data in URLs, such as access tokens, user IDs, or session identifiers.
3. RSA (Rivest-Shamir-Adleman)
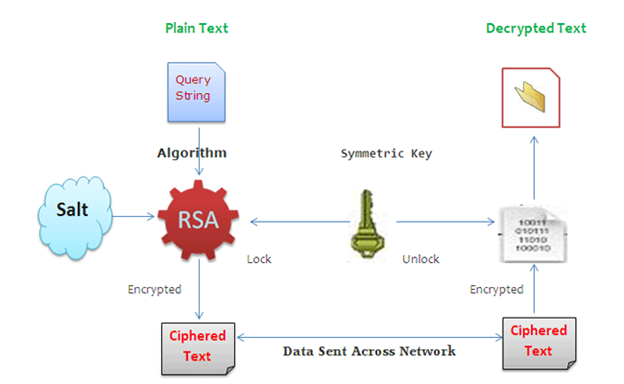
Description
RSA is a widely used asymmetric encryption algorithm designed for secure data transmission. It relies on a pair of cryptographic keys: a public key for encryption and a private key for decryption. Unlike symmetric encryption, RSA does not require both parties to share a single secret key, making it ideal for secure communications over public networks.
When used for securing URLs, RSA ensures that sensitive data can only be decrypted by the intended recipient, providing robust protection against unauthorized access.
How It Works
Key Generation:
Encrypting URL Content:
Transmitting the URL:
The encrypted URL is sent to the recipient over public or private channels.
Decrypting the URL:
Pros:
Strong Encryption:
No Shared Secret Key:
Secure for Public Channels:
Versatility:
Non-Repudiation:
Cons:
Slower Than Symmetric Algorithms:
· RSA is computationally intensive and slower compared to symmetric encryption algorithms like AES, especially for large amounts of data.
Use Case:
Sharing sensitive URLs in secure communications, such as email invitations or encrypted download links.
4. Base64 Encoding
Description
Base64 encoding is a technique used to encode binary data into a text format, making it suitable for transmission in URLs. Although not an encryption method, Base64 ensures URL-safe encoding by replacing non-printable characters with alphanumeric symbols. It is typically used for obfuscation rather than encryption.
How It Works
Encoding Data:
Sensitive URL parameters are encoded using Base64 to convert them into a URL-safe string.
Appending to URL:
The encoded string is appended as a query parameter.
Decoding:
The receiver decodes the string back to its original form.
Pros
Cons
Use Case
Obfuscating non-sensitive data in URLs for improved readability.
5. URL Tokenization
Description
Tokenization replaces sensitive information in URLs with unique, non-identifiable tokens. These tokens map to the original data stored securely on the server, reducing the risk of exposing sensitive details.
How It Works
Generate Token:
Store Mapping:
Append to URL:
Token Validation:
Pros
Cons
Use Case
Temporary access URLs for password resets or file downloads.
6. SHA-3 Hashing
Description
SHA-3 is a secure cryptographic hashing algorithm that generates fixed-length digests. When used with URLs, it ensures data integrity by creating a hash that can detect any tampering.
How It Works
Generate Hash:
Append to URL:
Verify Integrity:
Pros
Cons
Use Case
Ensuring the integrity of signed URLs in APIs.
Conclusion
In an era where data privacy and security are paramount, securing web URLs has become an essential practice for protecting sensitive information and ensuring trusted communication over the web. Each algorithm discussed—HMAC-SHA, AES, RSA, and others—offers distinct strengths and is suited for different use cases.
Selecting the right algorithm depends on the application’s requirements, including the need for encryption versus validation, computational efficiency, key management, and the type of data being transmitted. Combined with HTTPS and proper security practices, these algorithms form a strong foundation for protecting web URLs in today’s digital landscape.
References
These resources provide comprehensive insights into each algorithm, guiding developers and security professionals in implementing secure web URL practices effectively.
